Created: 11/06/2024 11:54 Last Updated: 07/01/2025 21:08
Our system exploited by PrintNightmare vulnerability. You should investigate the case.
~~Log Files (pass: infected): Download~~ Log Files (pass: infected): C:\Users\LetsDefend\Desktop\Files\PrintNightmare.zip
Note: You can use "Redline" for investigation
This challenge prepared by @Bohan Zhang
Looking through the alerts in Brim, what is the vulnerability name and its corresponding CVE?

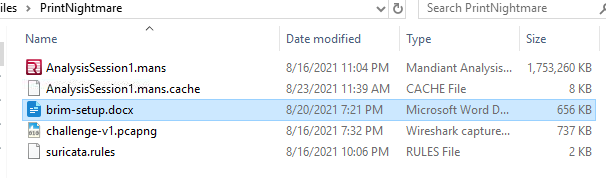
To answer this question as it intended, There is a brim setup guide for us to follow inside extracted folder
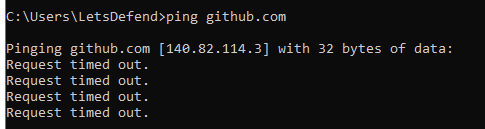
Since built-in VM for this challenge couldn't download brim suricata then we need to use another way to solve this challenge
And I was lucky enough to download challenges file when it was available on challenge description (go back to challenge description to download it) so I'll analyze them locally
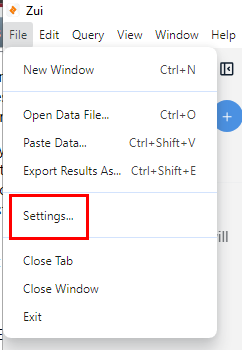
Open Zui Desktop (Brim) then go to "File" -> "Settings..."
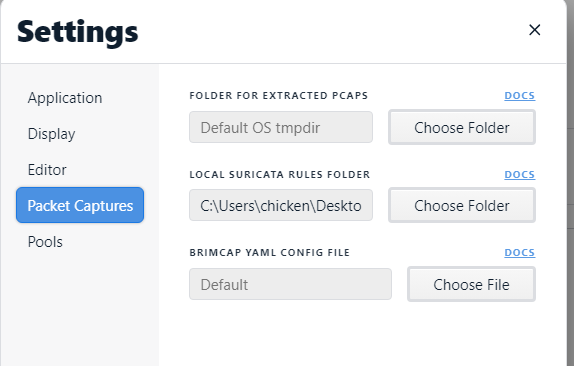
Go to "Packet Captures" -> "LOCAL SURICATA RULES FOLDER" and select a folder that stores suricata.rules
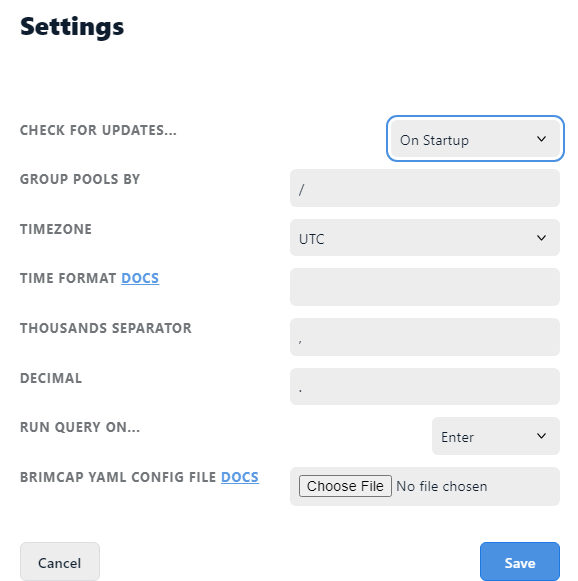
If you tried to do this on built-in vm (Zui 1.7.0), you will find that there is no suricata rule importing inside Settings menu... so get files to investigate locally or make VM be able to connect to the internet for updating
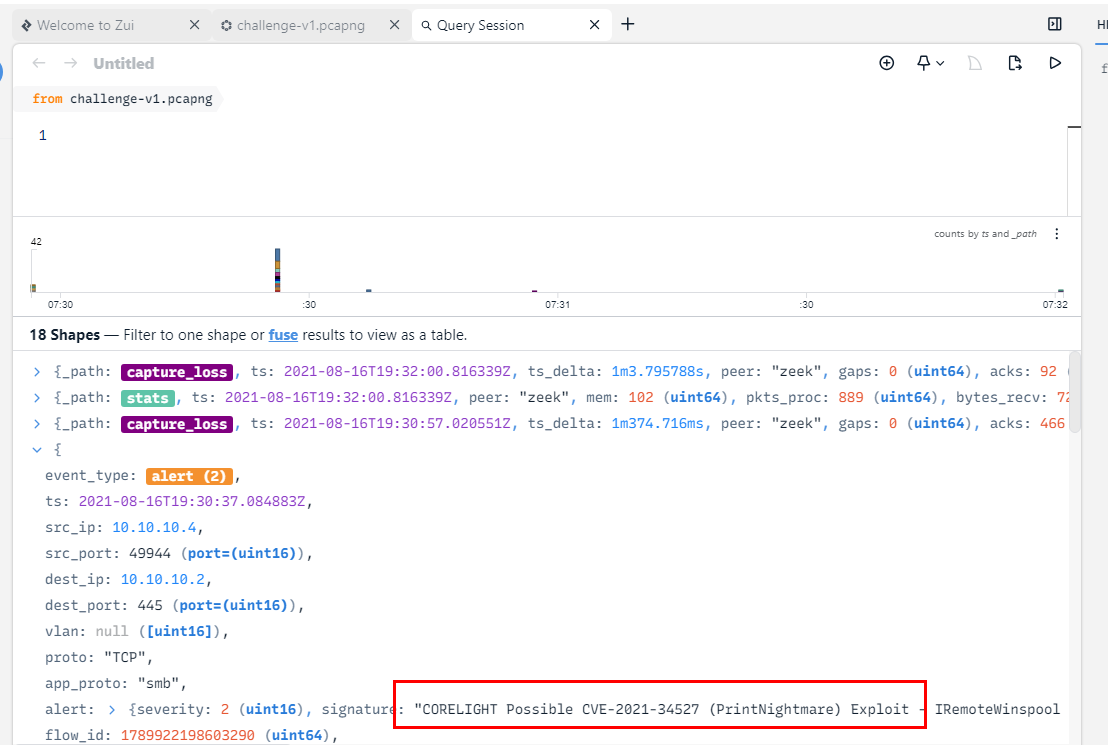
Load Data then enjoy Brim security with custom Suricata alerts which you can see that it worked well when inspect this alert event telling us that there were an exploitation of CVE-2021-34527 priviledged RCE vulnerability that let threat actor execute any commands as SYSTEM
PrintNightmare, CVE-2021-34527
What is Attacker's IP?
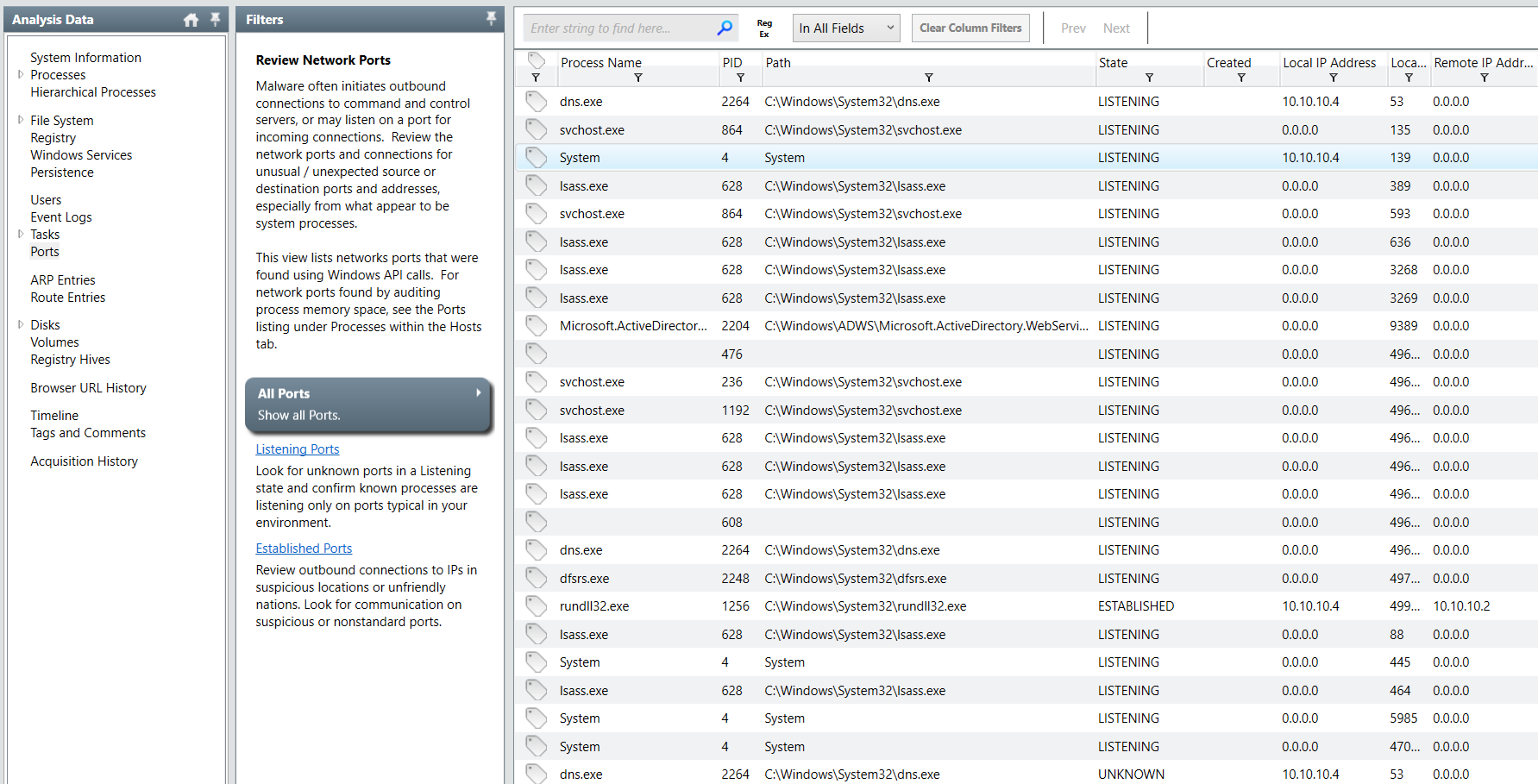
We already know how this vulnerability works and when you inspected process in memory dump file captured with Mandiant Redline then you can see that SYSTEM process has a connection to threat actor IP address
10.10.10.2
What is Attacker's share path?
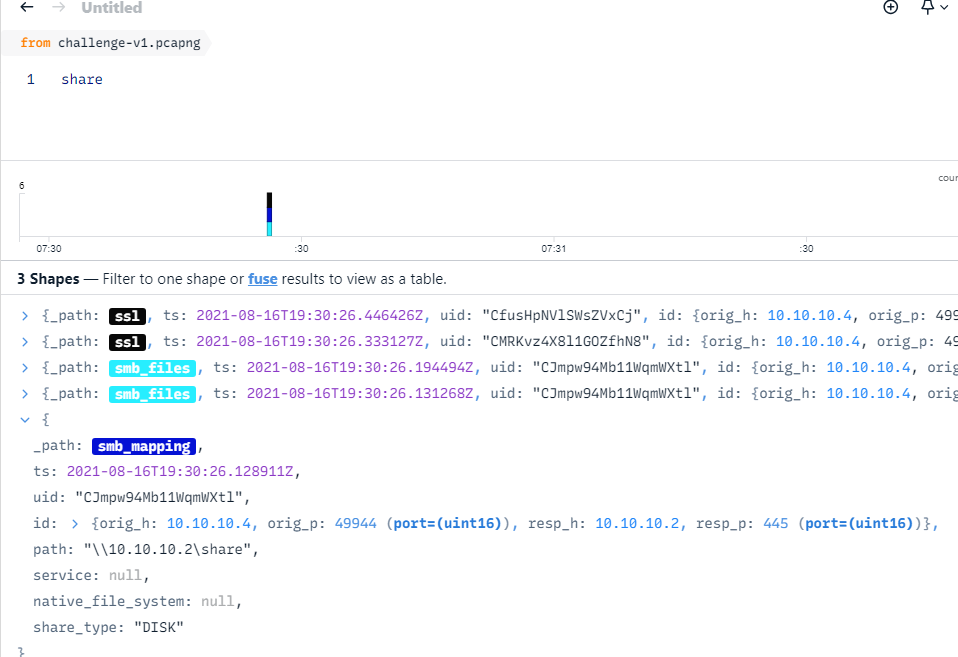
In Zui, search for share or smb then you will see the path of the share
\\10.10.10.2\share
What is the name of the malicious DLL file hosted by the attacker?
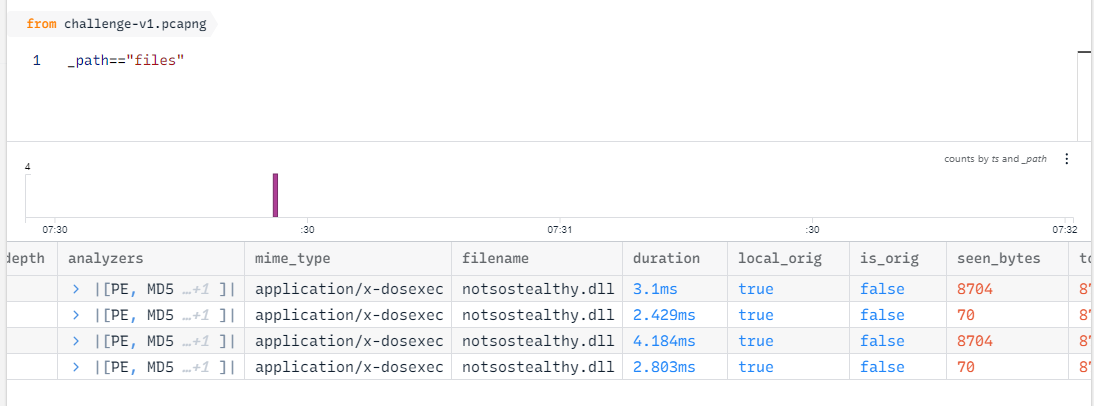
Searching for files and we can see that there is only 1 dll file detected from this pcap
notsostealthy.dll
What is the MD5 hash of the DLL file?
8ac469b77518820bbf0603a9ad56691d
What is the email address used for the self-signed SSL Certificate in the traffic?
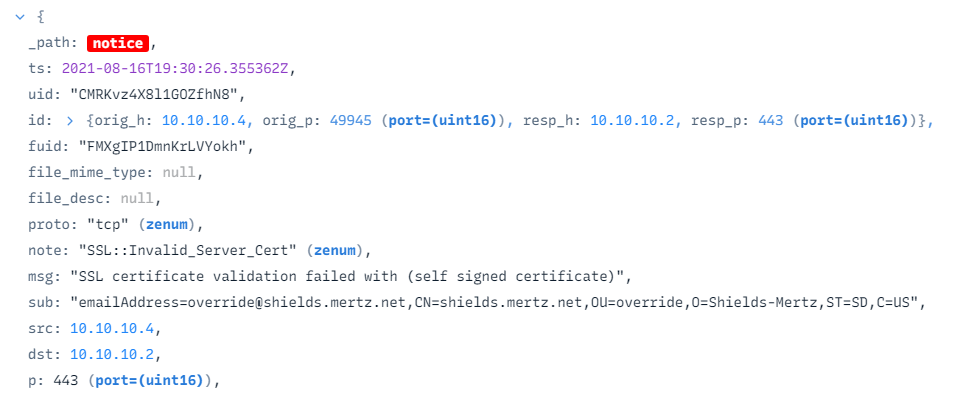
override@shields.mertz.net
What is the domain user used by the attacker to exploit the vulnerability?
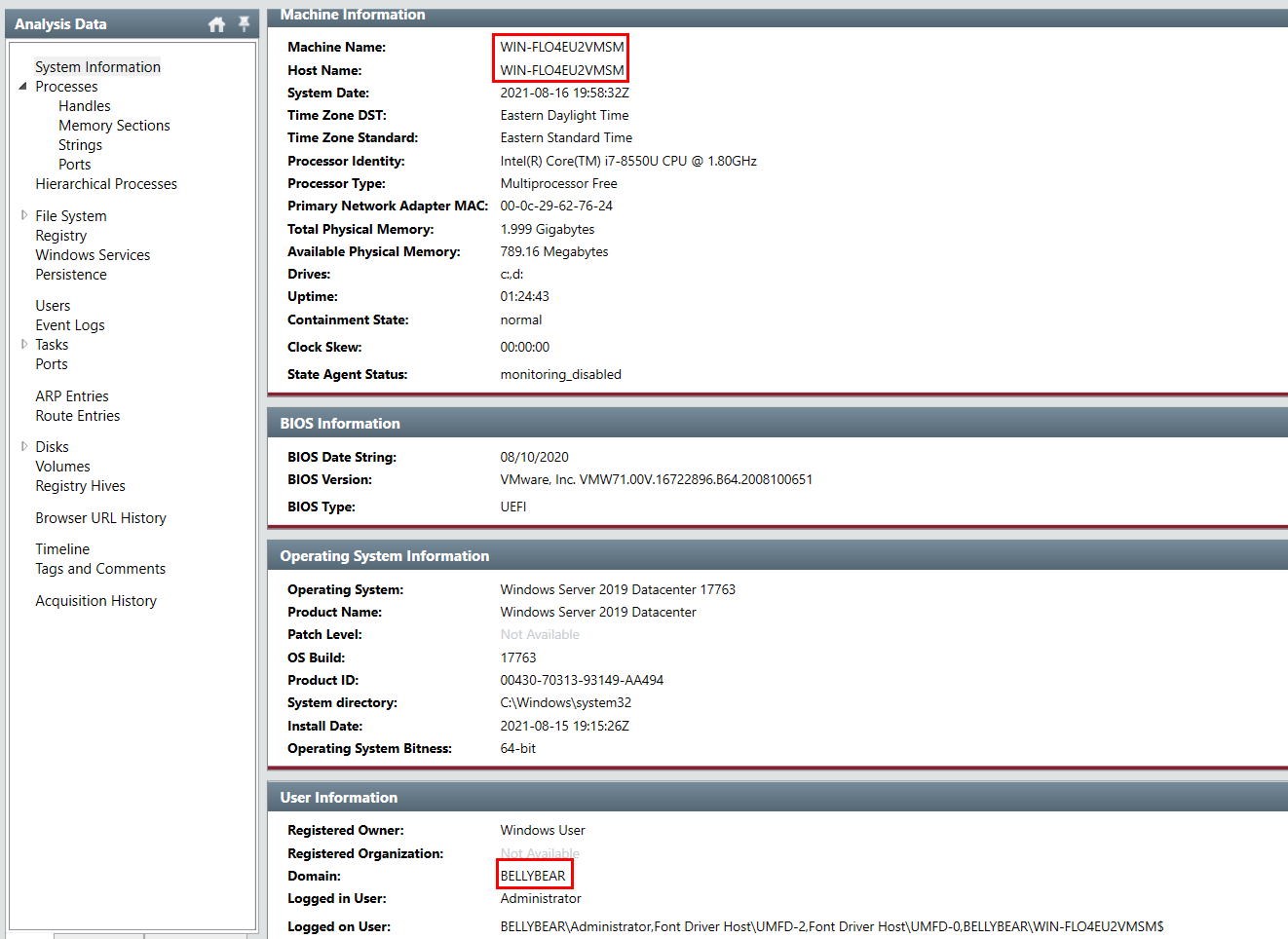
Go to "System Information" then we can see which hostname that vulnerable and exploited by threat actor including domain
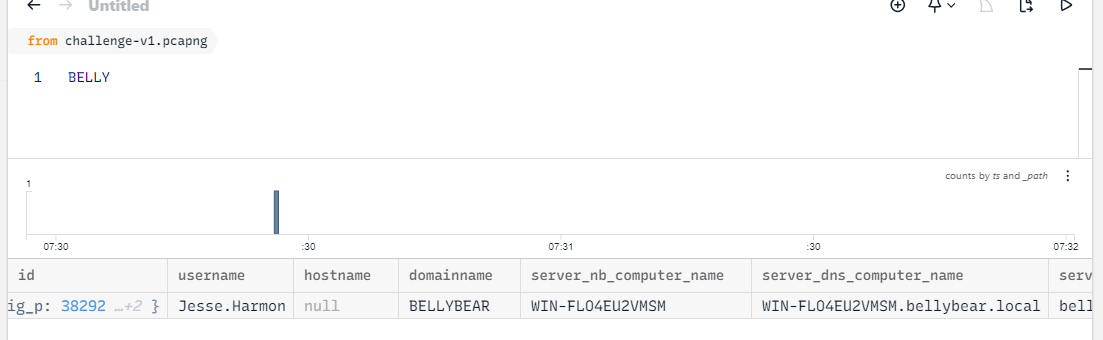
We got domain from Redline now we can search it on Zui to find username that was used to exploit
BELLYBEAR\Jesse.Harmon
What is the exploit server's hostname?
WIN-FLO4EU2VMSM
What is the username created by the attacker for persistence?
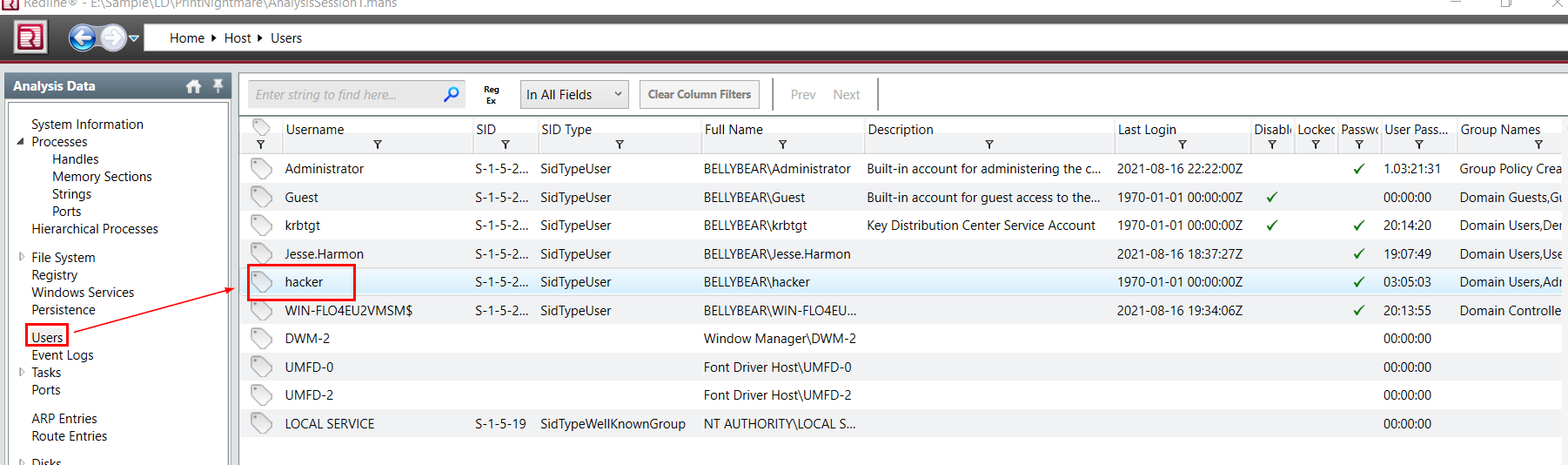
Go to "Users", which you will find hacker user that has the weird Last Login time
hacker
What is the event ID for user creation in Windows, and when was the user being created?
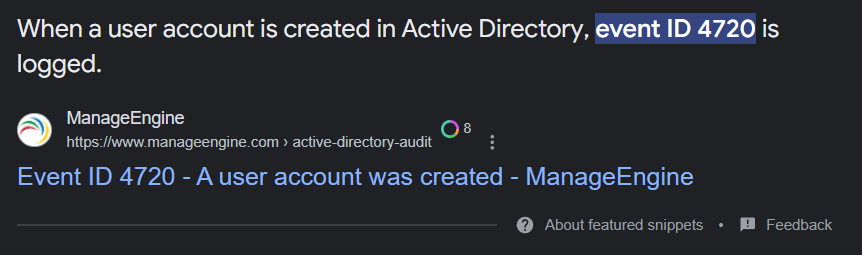
user creation in AD can be searched on event log with event ID 4720
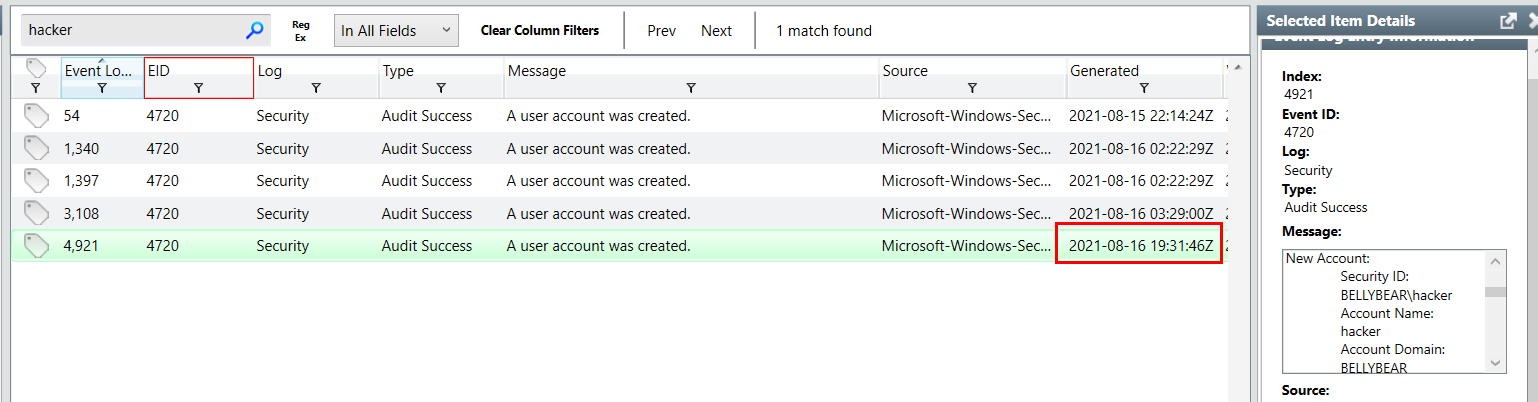
Filter for both keywords then we will have the time this log was generated and timestamp when this user was created in details
4720, 2021-08-16 19:31:46Z
What process name is used to establish the shell connection between the attacker's machine and the Windows server? and what is the listening port on the attacker's machine?
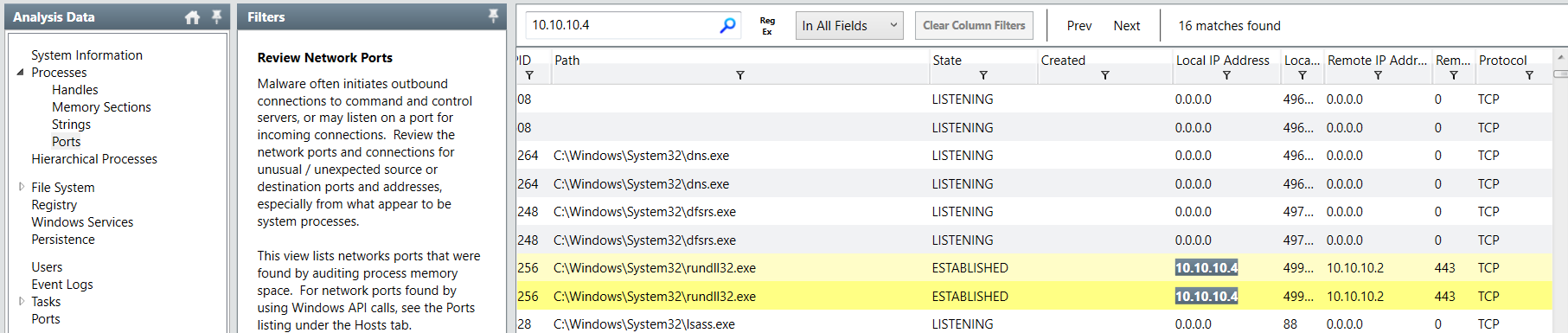
We know that the payload is dll file which mean rundll32.exe will be responsible for executing dll file and made a connection to threat actor C2, we can see that a port that being used for this connection is 443 (HTTPS) which make me think that a payload could be generated from msfvenom or metasploit
rundll32.exe, 443
The attacker used a famous post-exploitation framework to create the DLL file and establish the shell connection to the Windows server, what is the payload the attacker used?
So based on my skeptical, I searched on Google which payload could established a connection on port 443
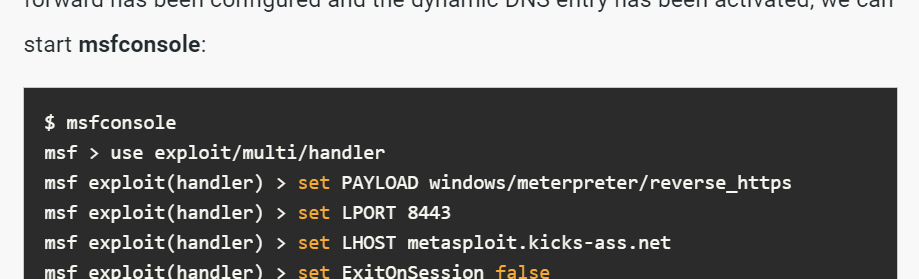
Which we can see that payload for this actually existed in metasploit framework but its not the right answer yet
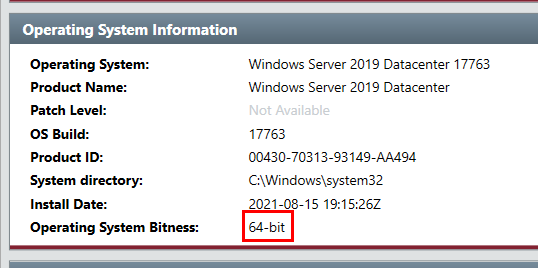
When I started learning penetration testing, one thing I remembered about Windows payload is there are 2 types of the same payload which are x86 and x64 architecture and after confirming architecture of this system then we can also determine which payload threat actor used for reverse shell connection
windows/x64/meterpreter/reverse_https
The attacker left a text file for the user Administrator, can you find what the filename is?
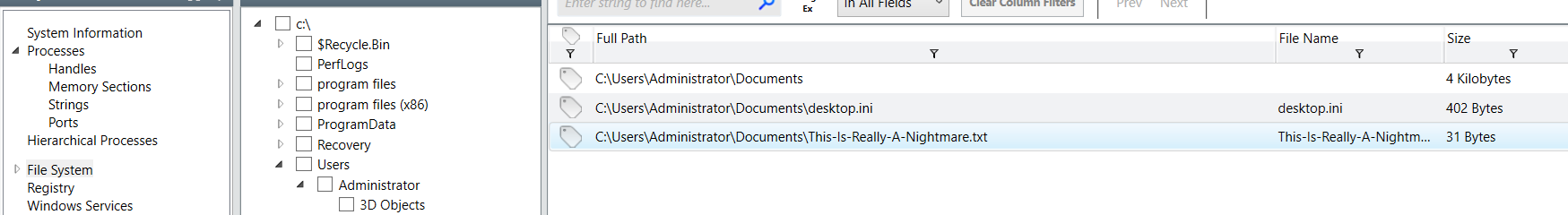
I found this weird text file inside C:\Users\Administrator\Document\ which is the one we're looking for
This-is-really-a-nightmare.txt
On this challenge, we learned how to import suricata rule into Brim/Zui for network analysis and with the memory dump image we can also determined which file, process, user and payload that the threat actor used to exploit PrintNightmare vulnerability and eventually created a new domain user for persistence and more